By now you should be having a fair idea of high usability of Oracle Application Express a.k.a APEX with its easy navigation between pages using column links, branches, breadcrumbs, navigation tabs, etc. For example, in Person Details application you can click on edit icon on a person row which takes you to Edit page for editing and saving that person details. The navigation here is done through column link by setting P4_PERSON_ID page item on Edit page (4) with Person_Id column value. If you observe closely parameters appear on URL string, it looks similar to
http://apex.oracle.com/pls/otn/f?p=62577:4:7632245014057279::NO::P4_PERSON_ID:241
where 7632245014057279 is my session id, P4_PERSON_ID is page item and 241 is page item value.
If proper security is not enforced in preventing in URL tampering, user can change the parameter in URL say change Person Id value to 242 in above example, and get that person details. It wouldn't seem as a bigger problem if all the users have same access to information.
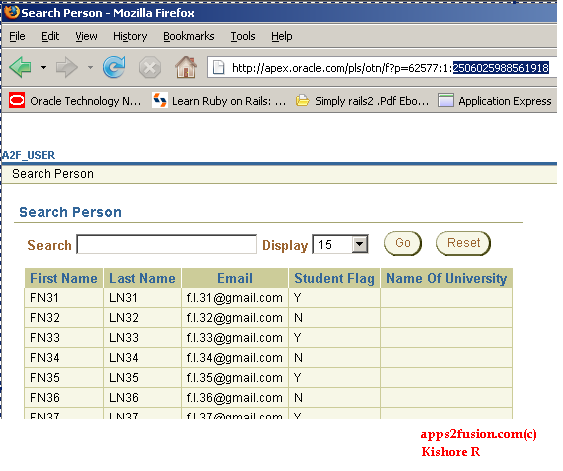
Consider this scenario I implemented in Authorization article, A2F_USER cannot edit/delete/create persons. When A2F_USER logins into Person Details application, he/she would not see edit/delete icons and create button as shown below.
Somehow if A2F_USER cleverly understood how APEX URL is constructed, he/she can add Edit page number (4), P4_PERSON_ID, its value keeping same session id and retrieve that person details. Though I used Authorization scheme to restrict A2F_USER from editing, he/she found out a way to edit by tampering the URL like this
http://apex.oracle.com/pls/otn/f?p=62577:4:2506025988561918::NO::P4_PERSON_ID:241
where 2506025988561918 is session id of A2F_USER. Using above URL, he/she can go to edit page
How to prevent URL tampering in APEX?
APEX has another built-in security feature called Session State Protection. This prevents users from tampering URL in your application. URL tampering can adversely affect program logic, session state contents, and information privacy.
You can enable Session State Protection for entire application or page or page item. Once it is enabled, APEX engine adds checksums in generated f?p= URLs. When user modifies the URL and submits it, checksums are computed again. As they differ from earlier checksums, error message is thrown and user is prevented from viewing information in the page.
How to enable Session State Protection?
Enabling Session Protection Protection is a two-step process. First, you enable the feature.
Second, you set page and item security attributes. You can enable Session State Protection from Session State Protection or Edit Security Attributes sections under Shared Components.
Steps to implement Session State Protection for Person Details application are:
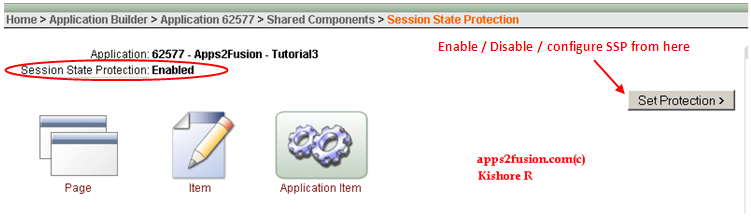
- Go to Shared Components > Session State Protection (Security section). Current Session State Protection status is shown.
Though status is already Enabled, it did not work in first place as it is not assigned to page or page items.
- You can click on Page / Item / Application Item, to assign session state protection. For our scenario, click on page. Select Page 4 and select Page Access Protection as 'Arguments Must Have Checksum'. Apply Changes.
You can also configure protection at item level.
Session State Protection is implemented for Edit page (4). Now if A2F_USER modifies the URL, he/she will see the message as "No checksum was provided to show processing for a page that requires a checksum when one or more request, clear cache, or argument values are passed as parameters"
See for yourself what happens when you login to Person Details application as A2F_ADMIN, click on edit icon to navigate to Edit page, modify Person_Id in the URL and hit Enter.
URL for the application:
My application can be accessed using the url http://apex.oracle.com/pls/apex/f?p=62577:1
Packaged Application:
My Packaged applications are created using APEX 3.2 version, you can only import them into APEX with same version. This packaged application has supporting objects i.e. table and sample data, along with apex application. You can import and run it without going through the above steps.
Download Packaged Application
Video for deploying packaged application (2:41 min). This video is applicable for deploying packaged applications for my next articles as well.
The zip file has sql files for application (apex_tut03_app.sql) and image (apex_tut03_img.sql).
You will learn more APEX 3.2 security features like hiding parameters on URL, etc. in coming articles.



Comments
The page is activated from a link in an email notification.
Do you have any guidance on what I can do to fix this to work like your application example?
Thank s,
Maggie
Thank you so much and I'm having a look forward
to touch you. Will you kindly drop me a mail?
my page https://Mypsyhealth.ru/, Mypsyhealth.ru: https://Mypsyhealth.ru/,
RSS feed for comments to this post