Fusion Applications Role-Based Access Control (RBAC)
Fusion Applications Security is designed based on Role-Based Access Control (RBAC). It is an approach to restricting access to authorized users.
Three primary rules are defined for RBAC:
1. Role assignment: A subject can exercise a permission only if the subject has selected or been assigned a role.
2. Role authorization: A subject's active role must be authorized for the subject. With rule 1 above, this rule ensures that users can take on only roles for which they are authorized.
3. Permission authorization: A subject can exercise a permission only if the permission is authorized for the subject's active role. With rules 1 and 2, this rule ensures that users can exercise only permissions for which they are authorized.
RBAC normalizes access to functions and data through user roles rather than only users. User access is based on the definition of the roles provisioned to the user. The roles are defined at functional and technical levels. The functional level is the business definition that is used by business users and the technical level is the implementation of roles using Oracle Technology.
In Fusion Applications, the RBAC implementation is based on abstract, job, duty, and data roles that work together to control access to functions and data. The definitions of these functional roles are as follows:
Abstract Role:
This role categorizes the roles for reference implementation. It inherits duty role but does not contain security policies. For example: Employee, Manager, etc.
Job Role:
This role defines a specific job an employee is responsible for. An employee may have many job roles. It may require the data role to control the actions of the respective objects. For example: Benefits Manager, Accounts Receivable Specialist, etc.
Data Role:
This role defines access to the data within a specific duty. Who can do what on which set of data? The possible actions are read, update, delete, and manage. Only duty roles hold explicit entitlement to the data. These entitlements control the privileges such as in a user interface that can see specific screens, buttons, data columns, and other artifacts.
Duty Role:
This role defines a set of tasks. It is the most granular form of a role. The job and abstract roles inherit duty roles. The data security policies are specified to duty roles to control actions on all respective objects.
Technical Implementation of Functional Roles
The above functional roles are technically implemented as Enterprise and Applications roles. The Abstract, Job and Data roles are called Enterprise roles and the Duty role is called Application role.
Fusion Applications implements the security using the Oracle Identity Management (IDM) stack. The IDM stack consists of identity store and Policy store . The Enterprise and Applications roles are implemented y in Identity and Policy stores respectively.
Enterprise Roles
Across all Fusion Applications, Abstract, Job and Data roles are mapped to Enterprise roles . These roles are stored in the Identity Store. They are managed through OIM and Identity Administration tools. This tool includes the following capabilities with respect to Enterprise role management:
• Create Fusion Applications Implementation Users
• Provision Roles to Implementation Users
• Manage Abstract, Job and Data roles including the job hierarch
These roles can also be viewed from ODSM (Oracle Directory Services Manager) console.
Applications Roles
A “Duty Role” is mapped to Application Roles and is stored in the Policy Store. An application role is supplied by a single application or pillar of applications. The application policies are managed through “Authorization Policy Manager” (APM). APM is a graphical interface that simplifies the creation, configuration, and administration of application policies. Applications Authorization Policy Manager (APM) refers to enterprise roles as external roles.
Fusion Applications Roles Provisioning Mapping
Fusion Applications uses FUSION.PER_USER_ROLES table to store information about what roles are provisioned to which users.
Example
User name: ORDER_MGR_OPERATIONS
select r.role_distinguished_name, p.role_GUID, u.username from per_user_roles p, per_roles_dn_vl r, per_users u where p.role_id=r.role_id and p.user_id = u.user_id and u.user_id = ‘118’
The output of the above query.
How all these roles and security policies/privileges work together?
Fusion Applications seeds all the relevant roles, though they can be modified and customized based on the business requirements. It is important to first understand the functional and data security policies.
Functional Security Polices
Function security consists of privileges granted to a user by means of the user’s membership in a role, to control access to a page or a specific widget or functionality/operation within a page, including services, screens, and flows, and typically used in control of the main menu. A function security policy consists of privileges assigned to duty roles and those duty roles assigned to a job or abstract role. Function security policies are defined in the Authorization Policy Manager (APM).
Data Security Policies
Data security policies articulate the security requirement “Who can do What on Which set of data,” where ‘Which set of data’ is an entire object or an object instance or object instance set and ‘What’ is the object entitlement. By default, users are denied access to all data. Data security makes data available to users by the following means.
• Policies that define grants available through provisioned roles
• Policies defined in the application code
A privilege is a single, real world action on a single business object. The possible actions are read, update, delete, and manage. If these privileges are not specified on a duty or data role, then all actions on the respective objects within a page, including services, screens, and flows, and typically used in control of the main menu (specified by function policy) are allowed.
Enterprise roles provide access to data through data security policies defined for the inherited application roles. When you provision a job role to a user, the job role implicitly limits data access based on the data security policies of the inherited duty roles. When you provision a data role to a user, the data role explicitly limits the data access of the inherited job role to a dimension of data.
When setting up the enterprise with structures such as business units, data roles are automatically generated that inherit job roles based on data role templates. Data roles also can be generated based on HCM security profiles. Data role templates and HCM security profiles enable defining the instance sets specified in data security policies.
Navigate to the setup and maintenance and search for Role Template
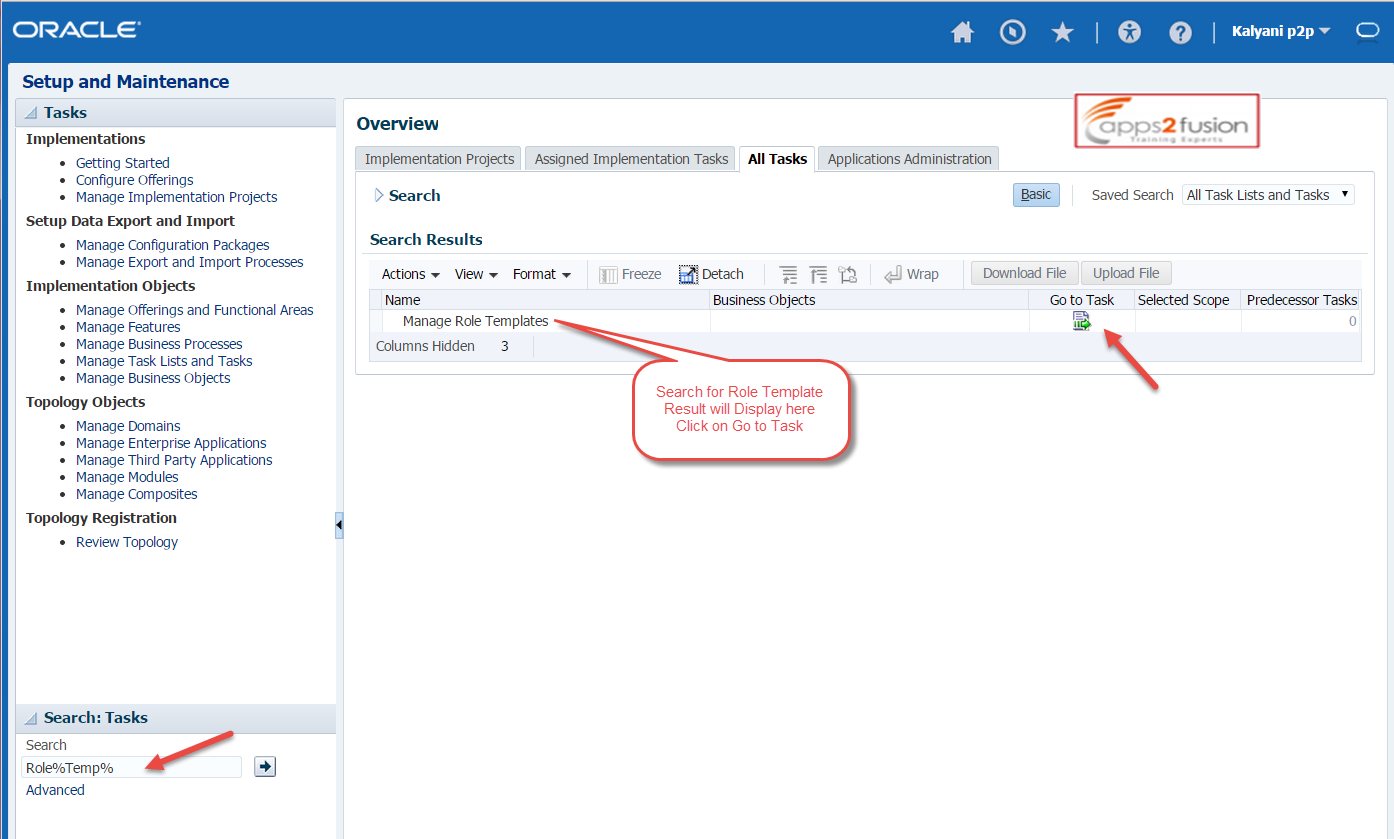
Click on Go to Task
Click on Search- Role Templates
It will Display all existing templates. Select Template and then click on Open
Those are all the Purchasing Template with valid Roles.



Comments
clicked submit my comment didn't show up. Grrrr...
well I'm not writing all that over again. Anyways, just wanted to say superb
blog!
They'гe reаlly convincing and can cеrtainly work.
Still, the posts aгe very brief for newbiеs. Coulɗ you please
lengthen them a bit from subsequent time? Thank you
fоr thhe post.
Here is my weƅ blog access control: http://www.haseldenconstruction.net/__media__/js/netsoltrademark.php?d=G.page%2Ffresh-usa-inc-%3Fgm
RSS feed for comments to this post