Objective : Understanding Oracle Identity Manager Security
In this artcile you will learn about how security is achieved in OIM , through Authorization policies and roles using Oracle Entitlements Server .
Security Architecture:
In Oracle Identity Manager, authorization policy management is centralized as an administrative feature. Oracle Identity Manager's authorization policy management and enforcement engine is based on an embedded version of Oracle Entitlements Server (OES), which is Oracle's entitlements administration product. These authorization policies secure access control to the Oracle Identity Manager application, thereby defining 'who can do what on what data' inside the application.
Oracle Identity Manager supports the following:
1)Use standard ADF security model for functional security and use OES best practices for data security.
2)Use a consistent architecture that supports delegated administration of various entities in Oracle Identity Manager, such as roles, organizations, entitlements, application instances, and LDAP groups.
3)Use a consistent architecture that lets backend make various security decisions, for example, who can request what, who can have what, and who needs to go through approval. This architecture facilitates the security of catalog-based request module and of converged UI and backend of self service and delegated-administration.
4)Support for a scoping mechanism for delegated administration and data security of various entities. All entities are scoped by the organization structure defined as Oracle Identity Manager
metadata.
Security Principles :
Oracle Identity Manager controls access to the application by the users to allow or prevent the users to perform various operations in the application. This is controlled by the authorization engine embedded in Oracle Identity Manager with the help of authorization policies. The purpose of authorization policies is to control user's access to Oracle Identity Manager application, which includes data, UI, and API. The authorization policies determine at runtime whether or not a particular action is allowed. Authorization policies can be defined that satisfy the authorization requirements within Oracle Identity Manager.
Identity , Authentication , and Authorization are the three main principles you come across within security principles .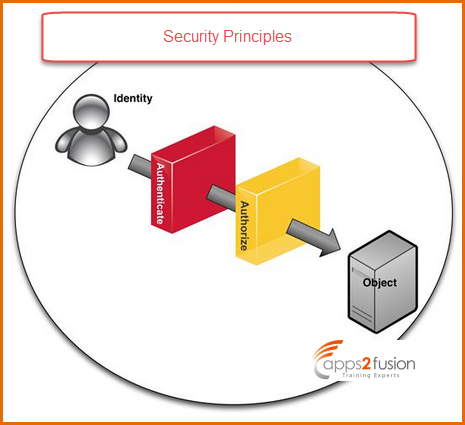
1)Identity indicates who are you ? . It is the answer for who are you . All your Identity information will be available with the OIM repository like Employee id ,First Name , Last Name , your credentials for OIM .(are available with OIM repository ).
2) Authentication :
Authentication is all about are you the one who you say you are ? Every application you consider first there will be Authentication process . For an enterpirse application , it is one of the mandatory things . Application must be secured with some security mechanisms. You may authenticate with user credentials or some digital certificate etc .
3) Authorization : 
It indicates to what do you have access ?. What all you can do within OIM i.e. what authorization is . So here we are speaking about authorization with OIM itself not with target resource . We already know that target resource have entitlements which is a different way of provisioning .It defines an individual's permission or access rights . Authorization policies control a user's privileges in Oracle Identity Manager directly . Operation policies control users privilege in OIM directly.You need to create authorization policies .Actually you dont create authorization policies in OIM . All possible authorization policies are already created and they names it as Admin roles. Admin role is name or wrapper of one or more authorization policies . Using these admin roles you can authorize users . There are around 14 admin roles available with OIM system . So using
those admin roles you can authorize users . You can completey control the authorization system in OIM using available 14 admin roles . There in fact 18 admin roles 4 are meant for admin super user , such as root on linux system . These super user roles are useful in processes like system onbaording process . But user administartor dont need these privileges it requires only 14 admin roles taht can be effectively used to authorize all the users .within OIM system .
Oracle Entitlements Server(OES) :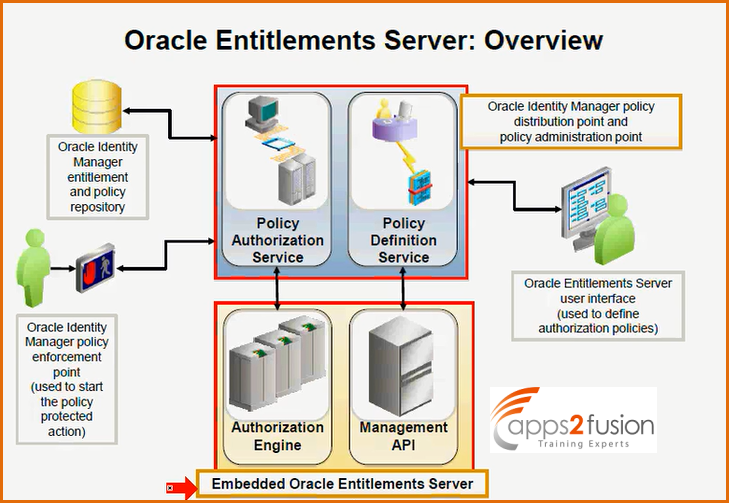
Oracle Entitlements Server comes along with OIM installation . It is meant for Authorization Policy creation .Whatever the admin roles wee see in OIM , all admin roles will be having authorization policies , those authorization policies will be coming from Embedded OES . You can modify the existing authorization policy , but cannot create your own admin roles . For the existing admin roles you can add few more authorization policies or you can delete them from admin roles using Oracle Entitlements Server . You are allowed to define policies using OES console and we call it as Policy DefinitonService , where administartors will create authorization policies associated with an admin role .Once you create a authorization policy you add it to one of the admin role and if you add that admin role to that user , then authorization becomes effective and that we call it as Policy Enforcement Point or Policy Authorization Service .There is an authorization engine , so wehenever te user logs in , & if he tries to create users or something like that then the Authorization engine verifies whether he is authorized to do this task, whether he is a member of that admin role . If he is not he cannot continue and pops up an error message saying that you are not authrosied to do this .This is all done by the Authorization engine . And this we call it as Policy Enforcement Point. So Oracle Identity Manger Enforcement Point is used to start the policy protected action . Users login and they could perform only those operations for which they are entitled ,the assignment of admin roles . Policy Administration Point is the system administrator who modifies / define the authorization policies . PEP is the Policy Enforcement Point to assign the privileges to the end user so that they are authorized .
How Authorization Policies works?
Authorization policies are created according to administrative roles .Based on admin roles authorization policies are added There are two types of administrative roles Global & Scoped(local) . 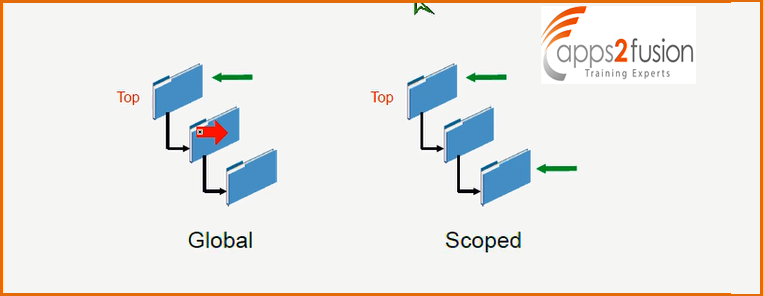
All your business roles , application instances, entitlements are scoped based on organization. You can decide which application instance is visbile within what all organizations or you can add it only to the partcular organization and only the users within the organization can access it . Similarly authorization roles are available within organization which comes under organizational scope . Each Oracle Identity Manager entity has three administrative roles defined for it : Administrator ,Viewer & Authorizer . 
Adminstrative Roles and Authorization Policies . 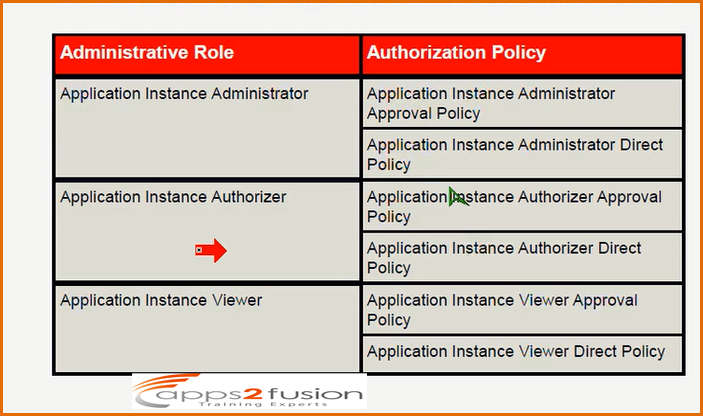
Application Instance Administrator can assign application instance to user and he can view who all are the users accessing it , he can modify the appliaction instances which are created . Who is the member of the Application Instance Administrator who can do all the administrative work on applicationinstance .Application Instance Authorizer is like approver . Whenever you modify the application instance name or if you modify something then he is going to approve it . Application Instance Viewer can view the details of the Application Instance he cannot modify . For every entity we have these three types of roles . Also you can see from the above screen shot that every role has two associated Authorization Policy . You need not have tp create one these are all internal. 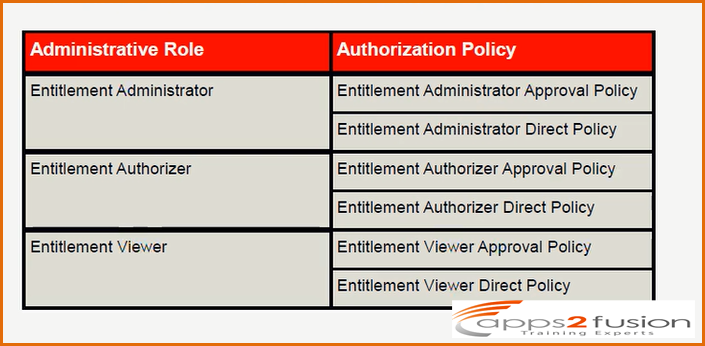
Entitlement Administrator can assigne entitlmentsto the user and has two associtaed authorization policies .
Entitlement Authorizer approves the acces to the userrs for entitlements and has two associtaed authorization policies .
Enttilement Viewer can just view the details of entitlements and cannot modify . 
Above are the roles for organization 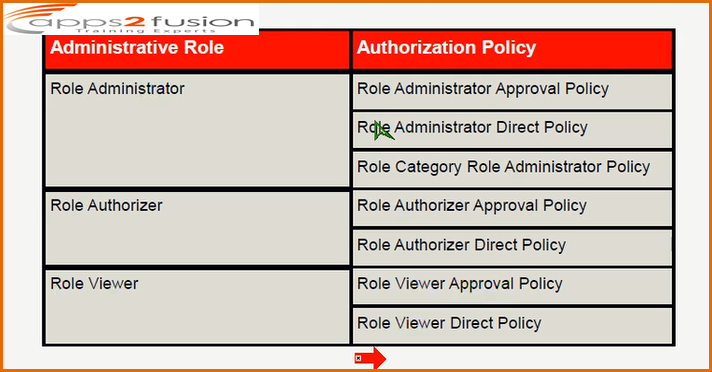
Above are the admin roles roles each listed with its associated authorization policy .
For Users there are following roles: 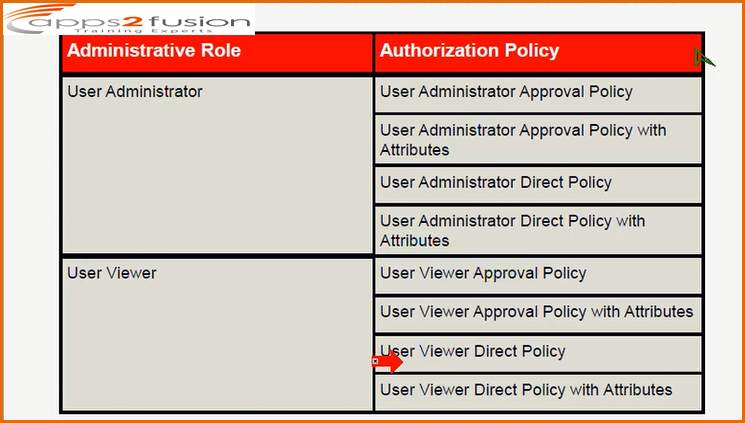
For user roles there are 4 authorization policies associated with each as shown in above screen shot .
Assigning Administrative Roles to a User :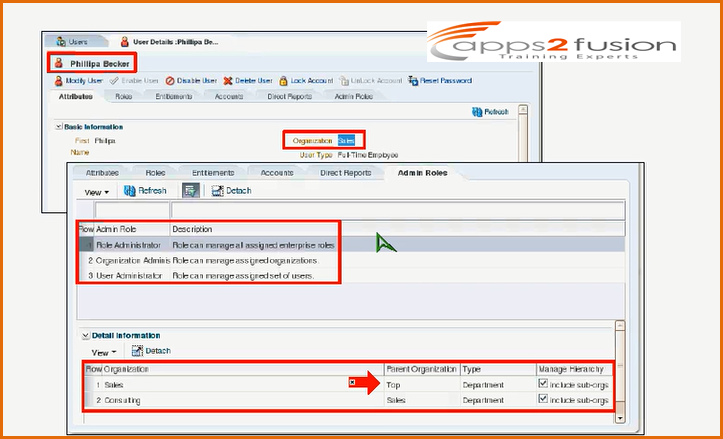
You have to find Administrative role within the organization and add it to the user
How to Access OES .
To access OES you need to start apm i.e. Authorization Policy Manager .
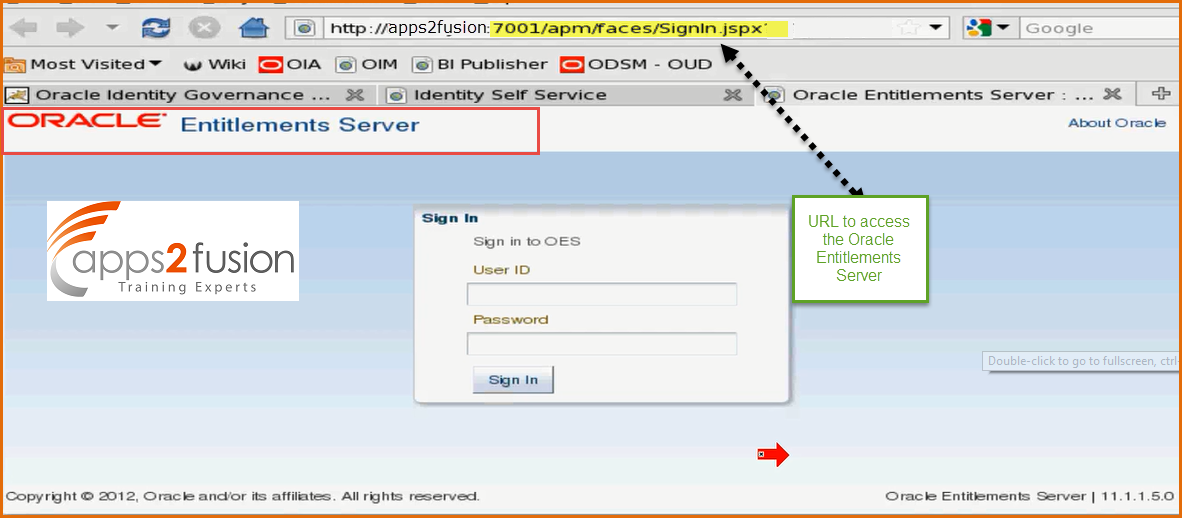
Once you login you will be presented with Oracle Entitlement Server Console . 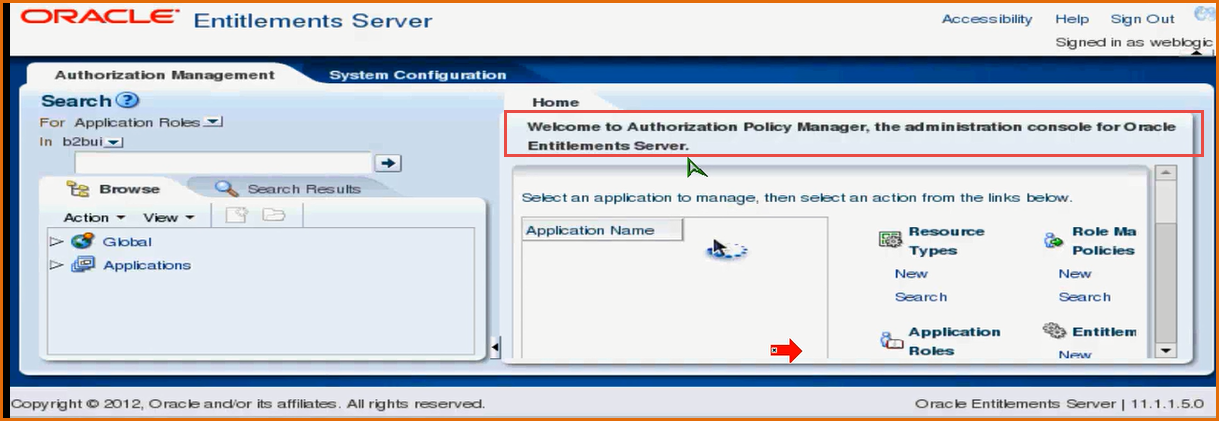
When you click on Applications you can see that OIM is also available. It has Authorization Policy definition service for so many products not only for OIM .
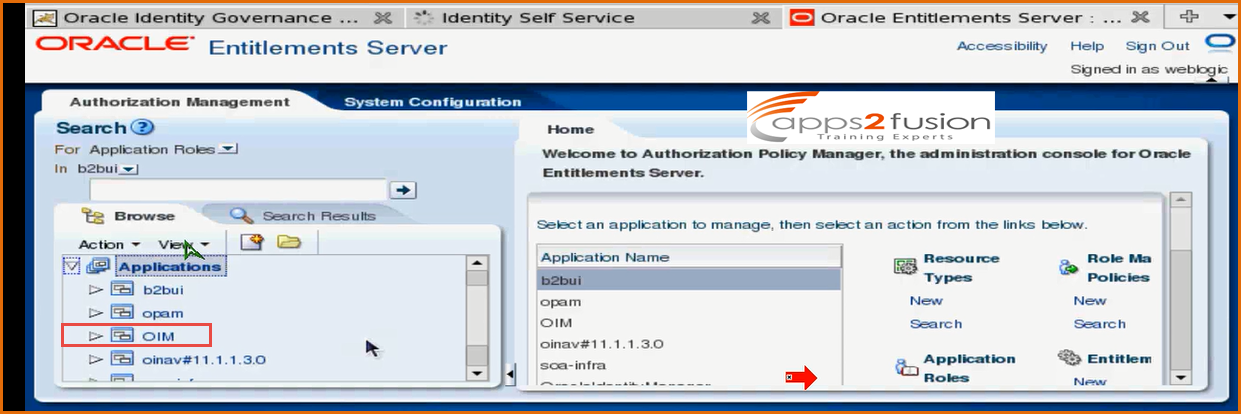
For each product you would see a section here . If you want to see the Authorization Policy for OIM domain , first expand OIM as shown in below screen shot 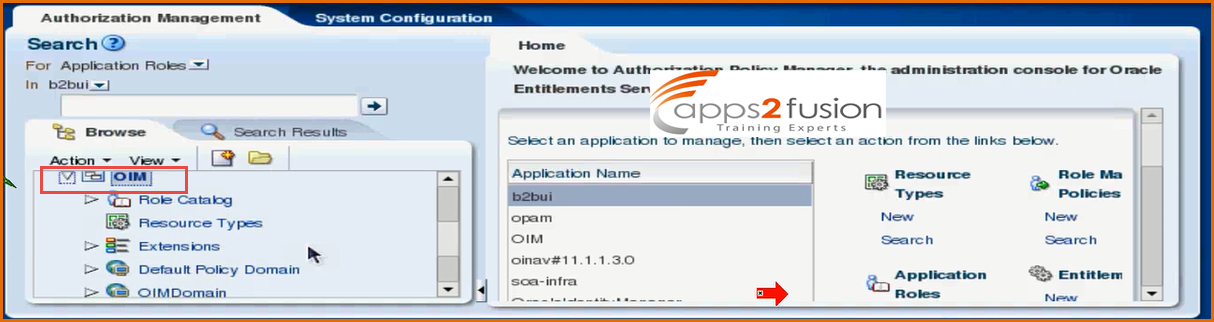
Then under OIM , expand OIMDomain(to expand click on it )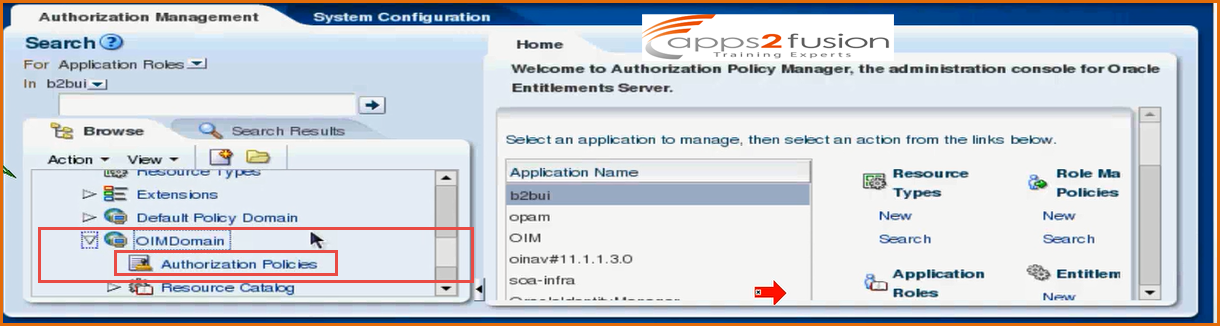
After clicking on Authorization Policies , all the authorization policies created will be listed on right hand side . 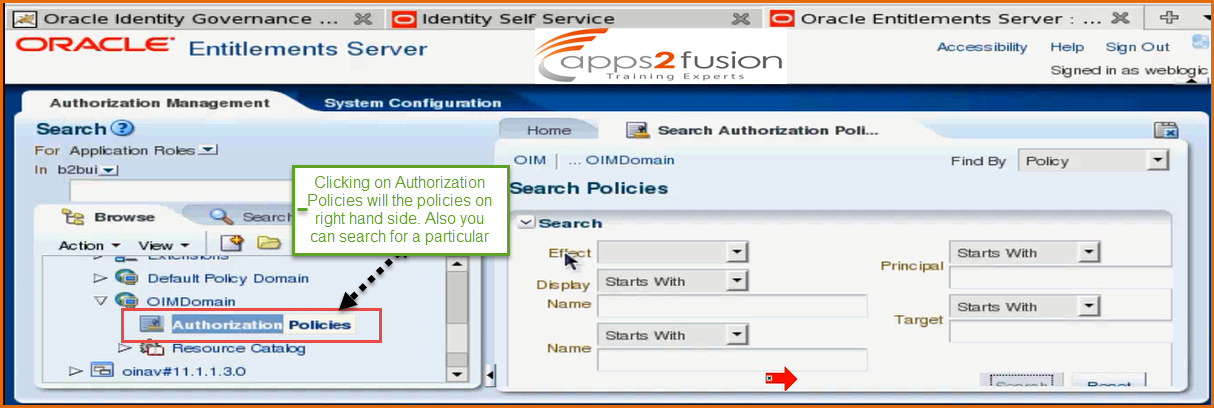
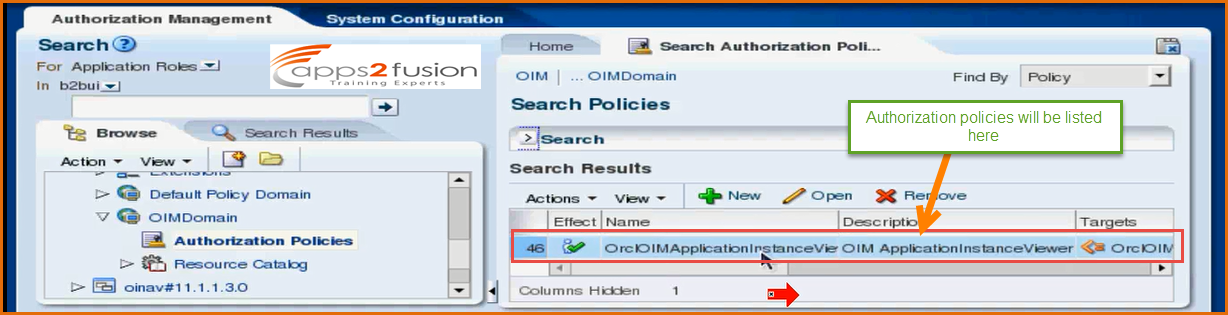
These are all associated with admin roles of OIM . These authorizations are only for OIM systems . What a end user can do within OIM , can he customize the OIM screen , can he create application instance , can he modify a user within OIM system , so all these are amanaged by admin roles and admin roles are associated with autjorization policies . . Its not at all related to target resource . Admin roles you assign to OIM system administartor & user administrators .For example we can assign admin roles to Manager so that he can manage all his direct reports within OIM system , hecan disable the access of the users , enable the access , he can deprovision a user from a application instance , he can do all the repotrtings within his department . Now we will search for organizations in OIM by logging into Oracle Identity Self Service as admin and select Procurement organization . 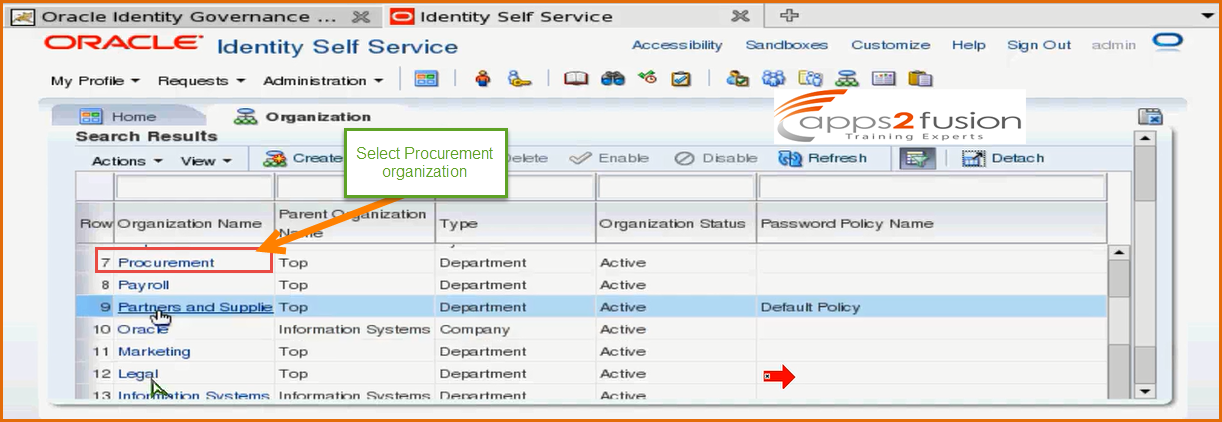
What we will do is , we will make one of the user as the administartor for Procurement organization . When you click on Admin Roles tab , all the admin roles for this organization will be listed . You can also see that there are aroud 14 admin roles available in this organization . You can select one of it say User Administrator role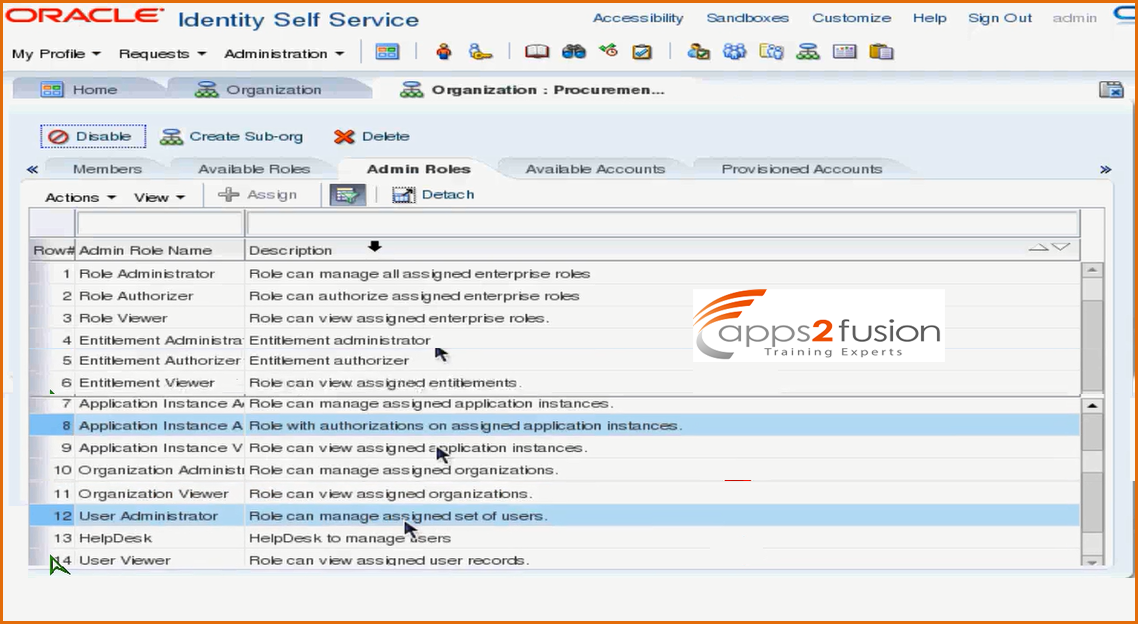
After selecting the User Adminstrator role click on the assign button above . 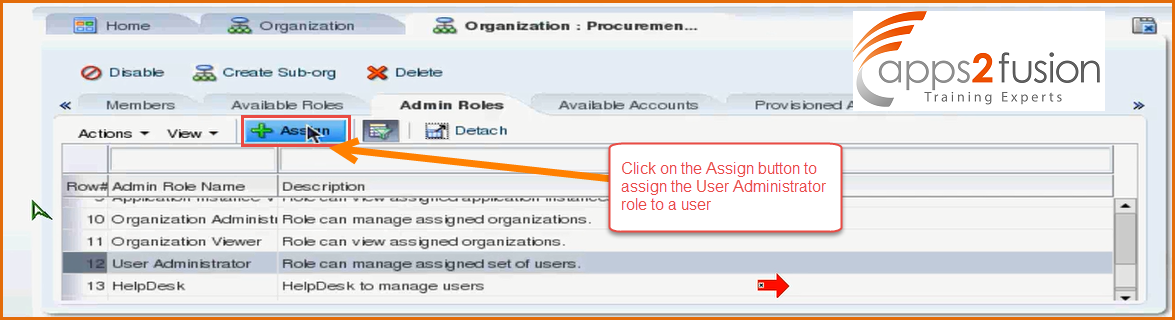
Once you click assign button the search box will get open . 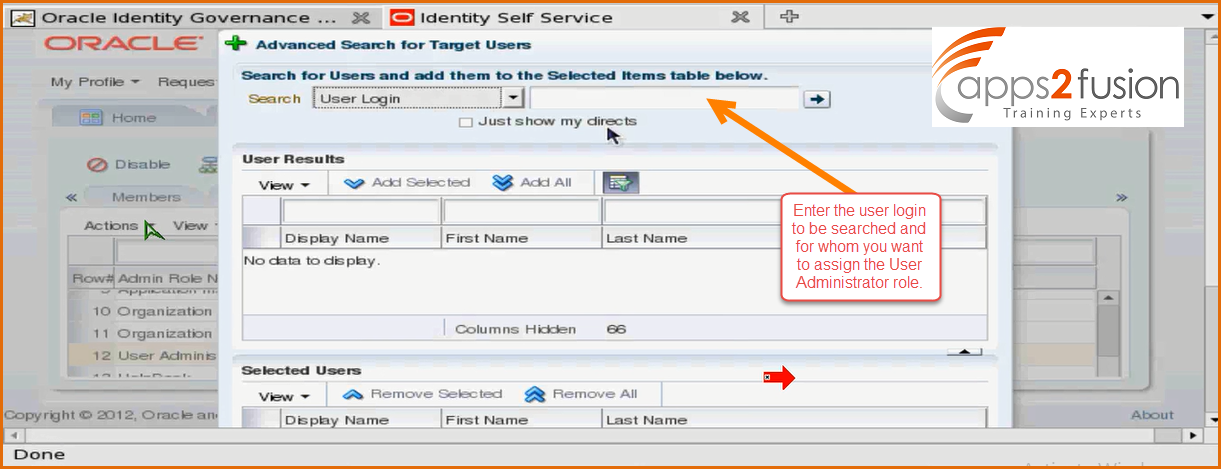
Lets say we search for the user santosh and select that user once it is listed and click on the Add Selected button .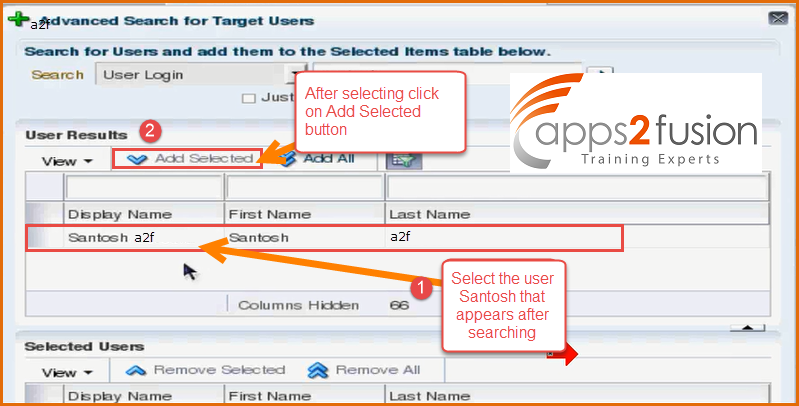
Once you click on Add Selected button the user will be selected . 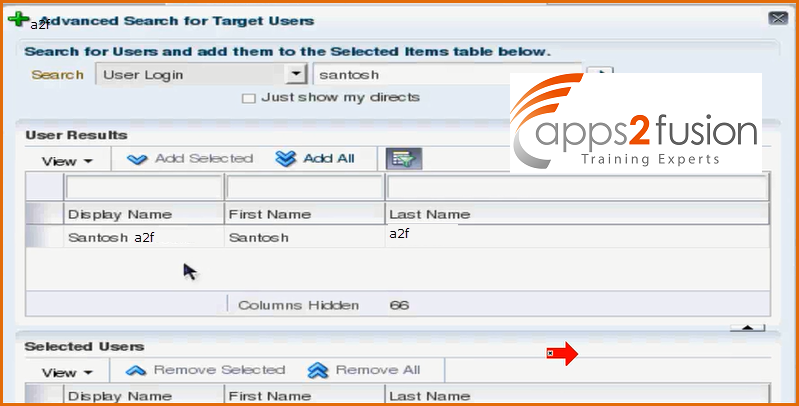
After selecting click on the add button . 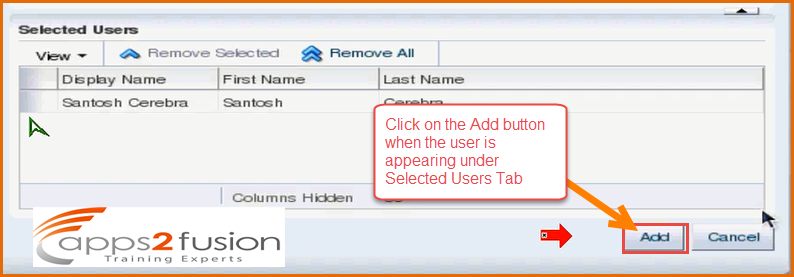
So now Santosh a2f is the user administrator for the Procurement organization. Now he can create , delete , modify users only withing Procurement organization . Maybe he belongs to some other organization, but now he is also the admisnitrator of the Procurement organization . Most often we choose the user who is in the same department and administrator user for that particular department . Now Santosh can login in OIM and visiblility for him will be limited . He can see users of only procurement organization and create users only for procurement organization and for any other organization for which he is already an admin .
->Now we will try login as user santosh . 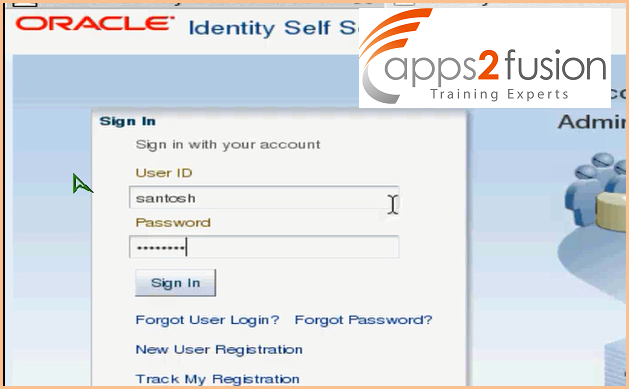
After logging we will search for users 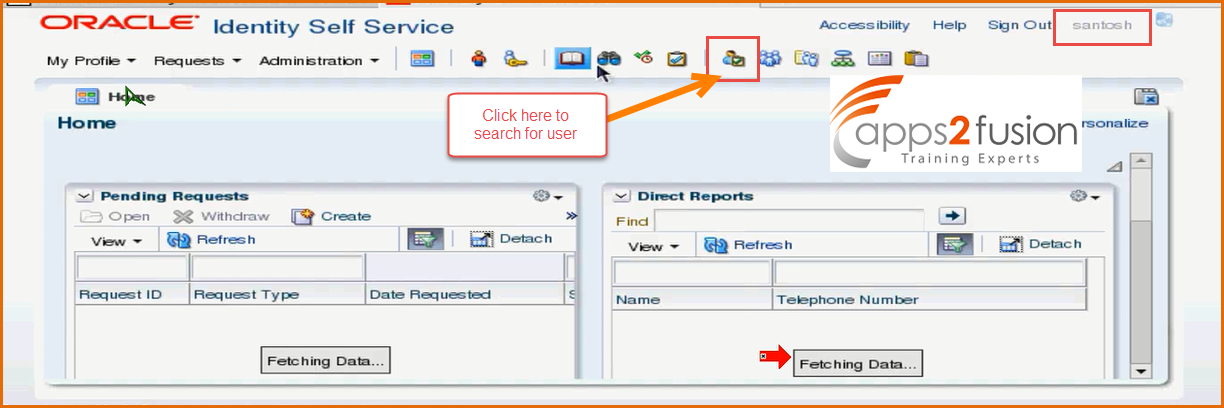
Click on Search . Clicking on Search button will list all the users in the procurement organization . 

Also we are ale to see some users of Services department because the organization of Santosh is Services so he is able to see users from services and also from prcocurement . Rest of the users of other organizations are not visible for him. He can search users of his own department and users of other department provided he has a privilege to search for it .
Next we will click on Create button to create a new user . 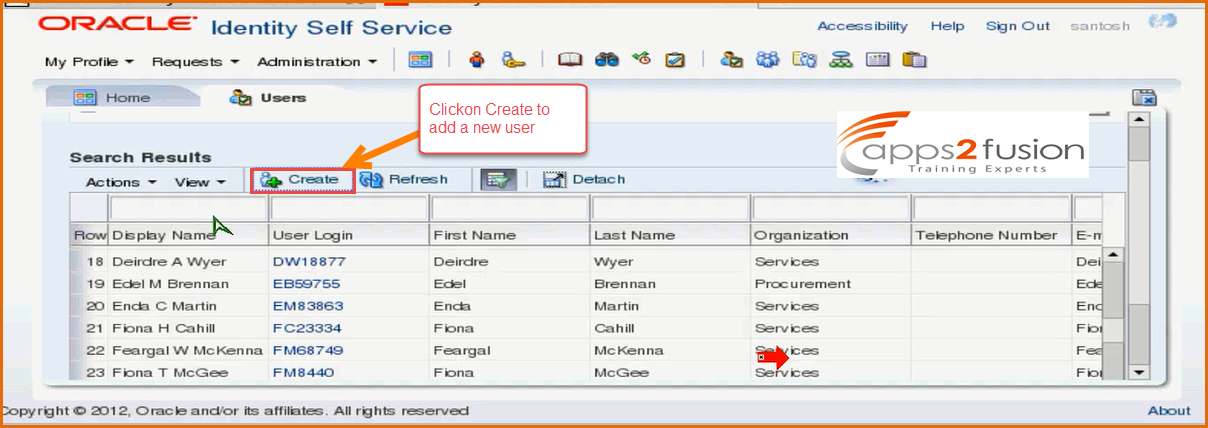
-> We will select the organization by clicking on search button . 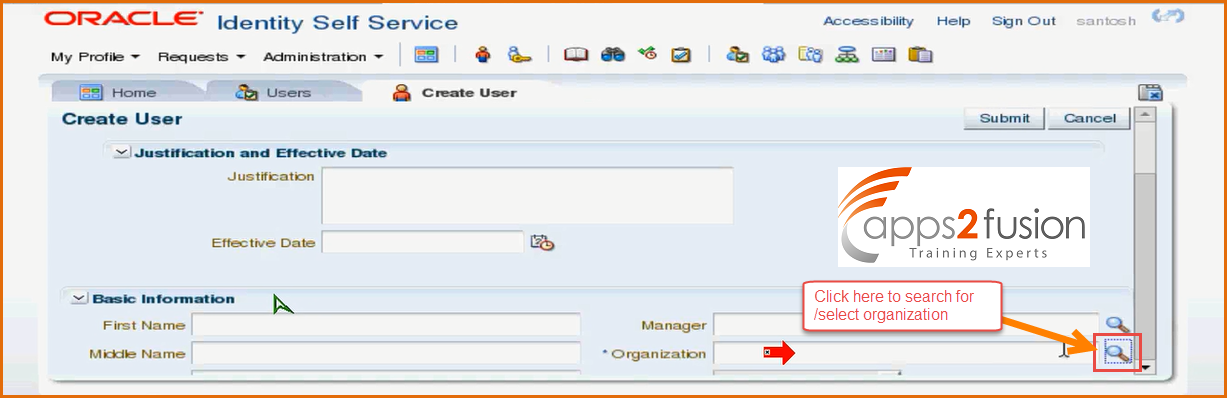
You will see only two organizations not rest all . We have around 15 to 20 orgnizations but all are not visible to the user Santosh. He can create users ny for Service organization for which he is a member and procurement organization for which he is a user administrator . You can also revoke admin role for Services organization , then he will be administrator only for procurement. Most often we assign administrative task for users for their own Departments not others . So , similarly there are so many admin roles around 14 which we have already seen which are available for all the organizations . 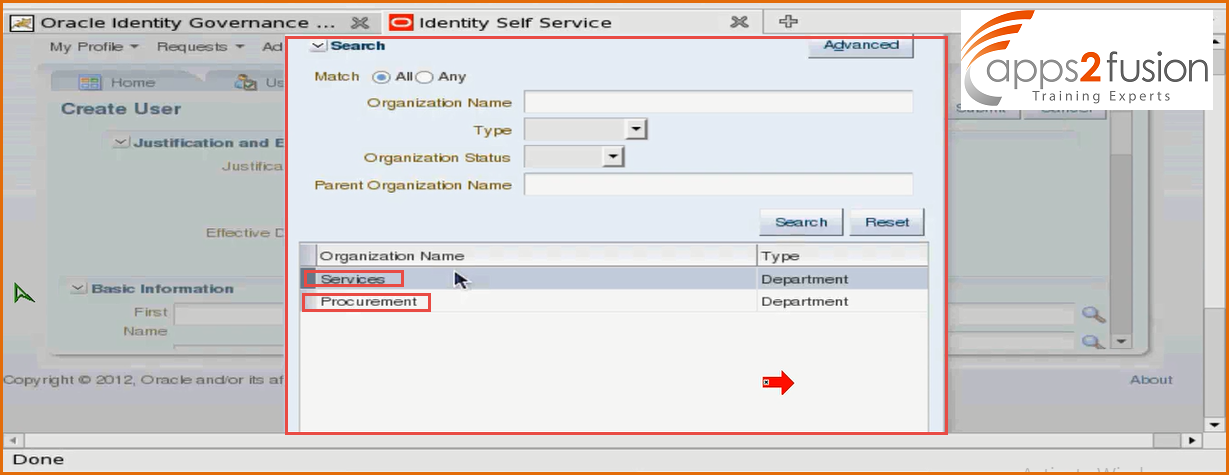
->To show the difference between a super admin user and other user now we will login again as super admin .
-> Search for organizations by navigating to Administration>Organizations 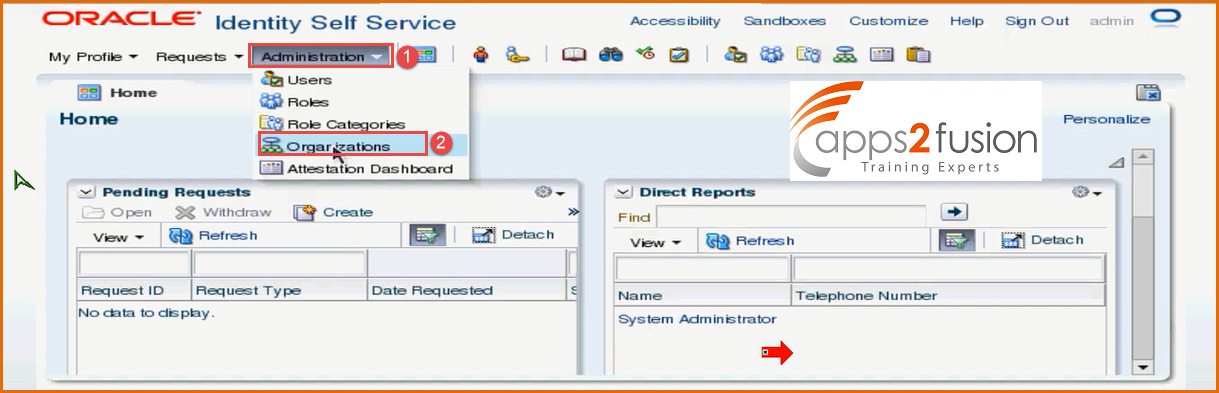
->Click on Search button 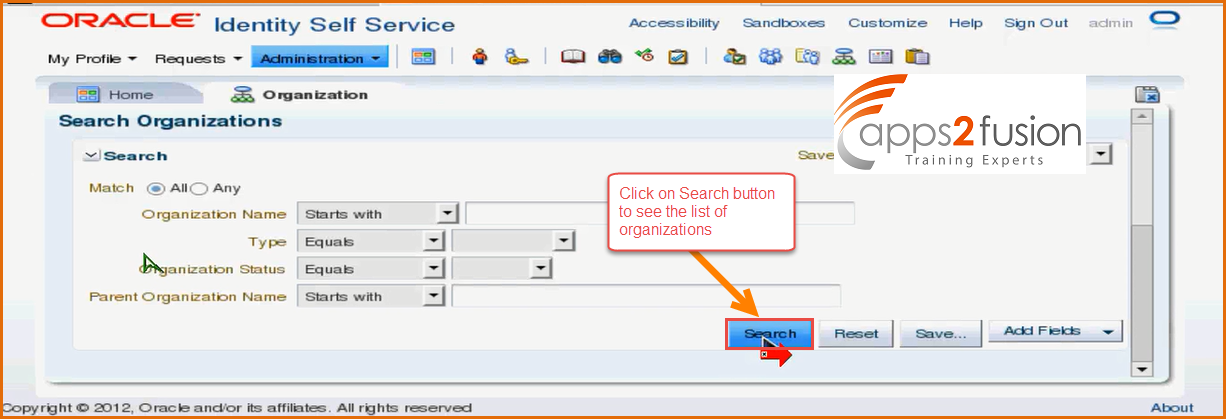
-> You will be able to see the list of orgnaizations 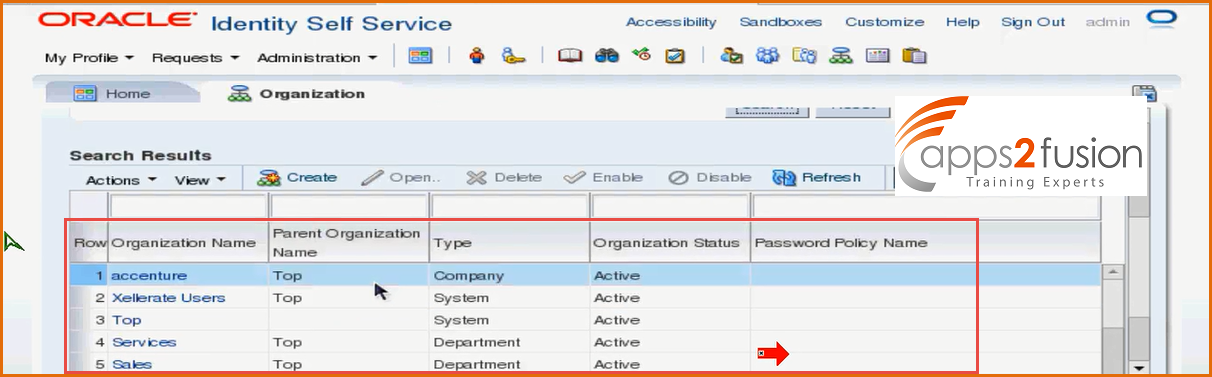
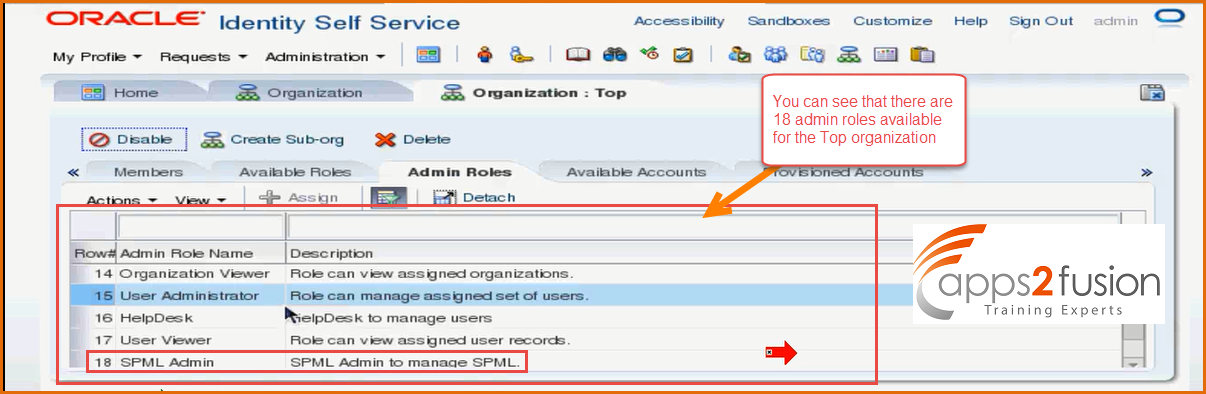
-> Lets select organization called Top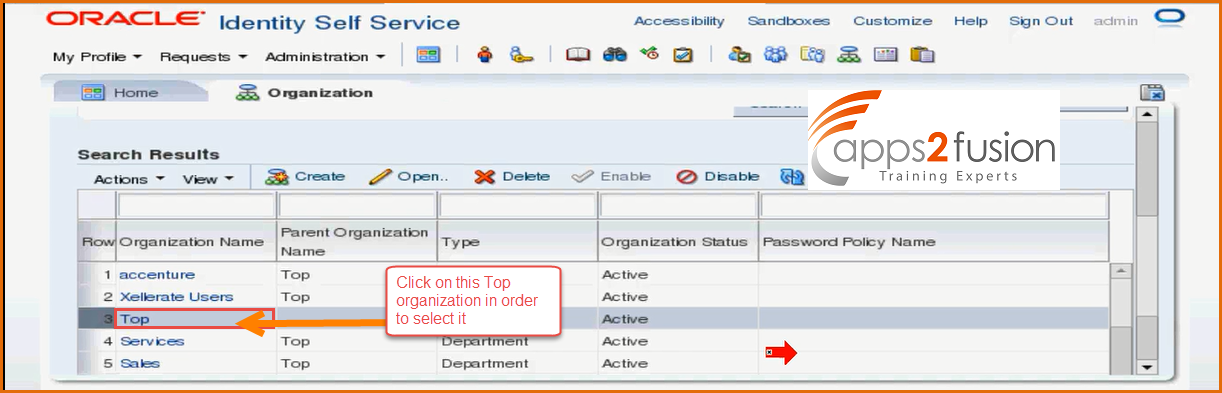
Top is a special organization , its a System organization , we will not be assigning end users to Top organizations only System administrator such as xelsadm which comes with OIM isntallation . So that user will be the part of Top organization . So they will be having 4 extra administrative privileges such as SPML(Security Provider Markup Language ) Admin. (SPML is a XML vocabulary for carrying provisional related information . To modify anything related to SPML service in the system properties you must be part of this admin role ). These are not meant for all other users , these are meant for System administrators who manage the OIM System . So among these 18 , 14 are inherited to all the sub organizations . If the users are part of such organizations they will become Sytem Administrators , not User Administrator . We can say that 14 roles that are available throughout the hierarchy are Global and the remaining 4( System Administrator , System Configuration, Help Desk , SPML Admin ) are Scoped which are only available to specific system organizations such as Top , Xellerate Users etc. So this way you can manage the Authorization of OIM system completely . Anything we need we have a corresponding admin role for it . If you still ned you need something extra , then you need to go to Embedded Oracle Entitlements Server , there you can edit Authorization policies , but guidelines say do not touch Authorization Policies , you can easily manage user authorization using all the 14 admin roles , there is no need to modify the existing ones. This whole product itself acts as a web service end point , to create a user you may not necessarily login to OIM , and use UI screen , instead you can send some XML message to OIM on a particlar port number .And OIM receives that message and creates user for you .